In This Article
What is Trusted Execution Technology (TXT)?
Trusted Execution Technology, or TXT, was formerly known as LaGrande Technology. It refers to the set of hardware extensions available on Intel CPUs and chipsets.
Technically, this technology helps in substantiating the authenticity of the operating system software and all hardware of the system cryptographically.
This ensures that every aspect of the computer system is running in a trusted space.
KEY TAKEAWAYS
- The Intel Trusted Execution Technology signifies the hardware extensions that ensure an improved digital office platform with better security capabilities such as protected execution and measured launch.
- This combination of hardware, software and firmware is designed according to the compliance of the Trusted Computing Group or TCG PC Client and Server specifications.
- The mechanism of Intel TXT is based on hardware but is capable of protecting the system from software-based attacks as well as the integrity and confidentiality of the created or stored data in the computer system.
- Intel TXT creates a setting where the apps and programs can operate in their own space and be secluded from all other software in the computer system to prevent them from malware attacks working on the platform.
- TXT cannot work without a Trusted Platform Module since it needs to store the measurements in it.
Understanding Trusted Execution Technology (TXT)
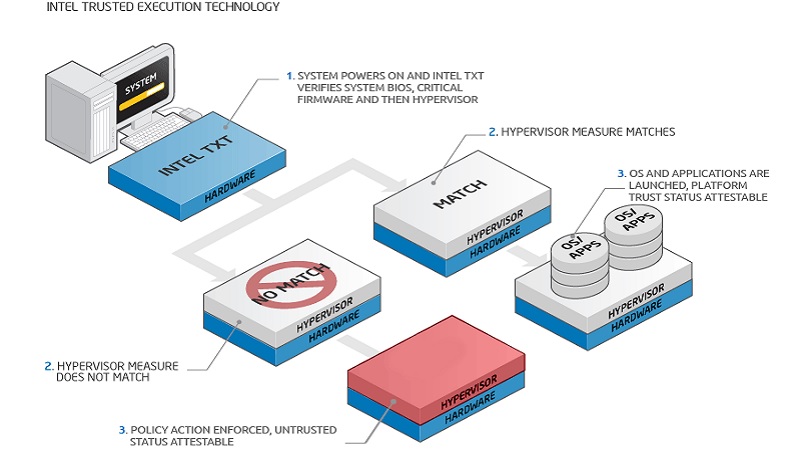
The Intel Trusted Execution Technology mechanism refers to the set of versatile hardware extensions.
These extensions are typically used to measure the components of the platform.
In simple terms, the set of extensions is a combination of different things such as:
- A set of security features
- A means to authenticate the features in use
- A means to measure and attest system code and configuration securely
All these help in building proper policies to create a trust level according to the measurements. These policies normally help in the following areas:
- Invoking improved capabilities for the system
- Preventing a system from entering the secure mode if it fails the policy
- Determining whether or not the system has entered and is working in a secure mode environment
This allows the software of the system and the remote and local management applications as well to utilize the measurements so that it is easier to make a trust decision.
Typically, the mechanism uses a Trusted Platform Module or TPM along with some advanced cryptographic techniques to offer a trusted environment and also complements Intel Management Engine.
This enhances the capabilities of the technology which involves:
- Providing a hardware rooted trust by creating a chain of trust to build the execution environment
- Protecting execution spaces used for processing sensitive data keeping them hidden from any other software
- Offering sealed storage shields to protect data and the encryption keys in use or stored from any external attacks
- Attesting the measurement of the operating software in the trusted and protected space
- Ensuring measured launch capability to reduce IT support costs, improve services, enable remote or decentralized computing, and verify platform configuration
- Protecting memory to improve utilization of system resources, increase the integrity and confidentiality of data, and improve data transfers and resources with the assurance of sensitive information protection.
These enhanced capabilities help TXT to promote safer computing and prevent the theft of data and sensitive information due to several conditions such as:
- Malware or any other software-based attacks
- Corruption in the system
- Basic Input Output System or BIOS corruption
- Modification of the configuration of the platform and more.
Most importantly, Intel TXT and its capabilities allow a large number of secure platforms to deal with the growing sophistication and frequency of software-based attacks.

Benefits:
Depending on different use models, the flexibility of Intel TXT and the benefits offered by it can be ascertained.
Local verification
Here, the measurement of the capability of TXT is used to allow the local users to use a platform with complete confidence and assurance that it is operating in a known and safe state.
This is because the technology measures the configurations launched accurately and stores them in the Trusted Platform Module of the platform.
Remote verification
Here the stored measurements in the TPM are taken into consideration to inform the remote entities that are not executing on the platform about the existing configuration of the platform.
The remote entities can depend on the properties and information provided by TXT, and accordingly, offer the protections as desired.
In order to make the best use of this technology, there are, however, a few specific requirements to meet. These are:
- A Trusted Platform Module to measure components of the firmware before running it on the board support package
- Signed Authenticated Code Modules or ACMs offered by Intel
- Proper processor and chipset support
What it provides:
Ideally, Intel TXT provides flexibility to the system so that the administrator can craft policies corresponding to the necessities of the datacenter.
Apart from that, it also enables attesting the servers that meet the terms of the particular trust policy. This helps in creating a pool of trusted servers that follow the specific trust policy.
What it does not do:
The technology does not evaluate trust and does not define its level either. This is because these terms are subjective and may change at any time.
In fact, it allows different entities to create their own trust decisions by using a set of stronger credentials that may or may not be based solely on TXT.
These entities include:
- Datacenters
- Cloud service providers
- Cloud service clients
- Operating systems and more.
In addition to that, the technology also does not track the runtime configuration but measures only particular events like Power On.
These are typically done only on a request made by the host operating system before a secure launch, and not by the guest operating system or its applications.
Should You Enable Trusted Execution Technology?
Ideally, Trusted Execution technology will work with matching software. It shouldn’t matter much if you turn it off, unless you are using it in a big corporate environment.
Moreover, this technology is not needed for BitLocker without a Trusted Platform Module because it can run with or without a TPM chip.
Typically, TPM is a dependency of TXT, but TXT is not. This means that TPM is the vital part of TXT, without which it cannot work.
Apart from that, every time you switch on your computer, you will be asked for a password to enter before you can get into the Windows login screen.
However, Windows offers the users with an option to either insert a USB key or enter the password manually.
The latter approach is much better because you will not have to depend for authentication on a single, specific USB key.
And using TXT for Bitlocker may also block the supported rootkits on the hypervisors.
Typically, Trusted Execution Technology is disabled by default. You will need to configure it according to the server service manual in order to enable it.
In any case, it is good to enable it because you may encounter some issues while giving some specific commands to the graphics card.
This happens because the IOMMU or the Input Output Memory Management Unit of the graphics card may be disabled.
How to Disable Trusted Execution in BIOS?
If Trusted Execution Technology is enabled in your system with Intel CPUs that support this technology, you can disable it easily by using the Intel TXT Support option.
This support can be disabled and prevented from working properly by disabling any of the following:
- All the processor cores
- TPM
- Hyperthreading
- VT-d
In order to disable these, the process to follow is:
- Go to the System Utilities screen
- Select System Configuration
- Choose BIOS/Platform Configuration
- Click on Server Security
- Choose Intel TXT Support
- Choose Disable
- Save the changes.
This will disable TXT support in your computer system.
Trusted Execution Technology vs TPM
- TXT needs the TPM to store the measurements of the platform or hash of components. On the other hand, a platform does not need to support TXT if it has TPM alone to provide the benefits offered by TXT.
- TPM is typically a dependency of TXT, but it is not true the other way around. Ideally, Intel TXT cannot work without TPM.
Conclusion
Intel TXT is a hardware mechanism that ensures the authenticity of the platform and the operating system.
When it is enabled, it ensures that the operating system is working in a trusted setting with added security.
Though this feature will be disabled by default, it is easy to enable it and enjoy its benefits.