In This Article
What is Windows Registry?
The Windows Registry refers to the storage that holds all related information, data, options, settings, and other values for the hardware and software installed on the PC across all versions of Microsoft Windows operating systems.
Technically, it refers to the centralized data storage in a hierarchical database structure. Its main function is to store the configuration settings of the apps and manage resources on the Windows operating system.
KEY TAKEAWAYS
- The Windows Registry is the official database for the system, where all vital data related to hardware and software is stored.
- This is the central source of data storage visited by users looking for fast data related to apps, programs, and others, thus saving valuable time.
- This specific registry can be used by the user interfaces, the security account services, the device drivers, as well as the third-party programs.
- Apart from providing faster access, the Windows Registry also helps in identifying system errors and monitoring system performance.
- The granular nature of the values in the registry offers a more customized user experience over and above the regular settings menu.
Understanding Windows Registry
Typically, you can consider the Windows Registry as a hierarchical database. You can say that, with all the contents of it, the Windows Registry is the DNA of sorts for the operating system.
It contains all data and information related to the settings and configuration of almost everything that is on your computer, such as:
- The hardware components
- The applications and programs
- The services
- The user account profiles
- The device drivers
- The user passwords
In addition to that, you will also find other relevant information regarding the device configuration, the respective tuning parameters, and user preferences.
The app settings are usually stored in separate files for each. The registry is the central place to find all the settings of all applications and is available in database form.
You can use the registry for much more than just settings, providing you with near-instant access.
In fact, the software and operating system refer to the Windows registry for the necessary information continually during its runtime.
The folders that you see in the Windows Registry are called keys, and their settings are more granular.
It consists of both codes and numbers. All these codes and numbers dictate settings that anyone can normally think of.
For example, they contain the definitions of how fast a letter would appear repeatedly on the screen when and if you pressed and held down the specific key to that letter on the keyboard.
In an ideal sense, users can have a much better user experience and a much faster PC by customizing the registry with the help of the Windows Registry Editor, more commonly referred to as regedit.
This is made possible due to the granular nature of the registry itself.
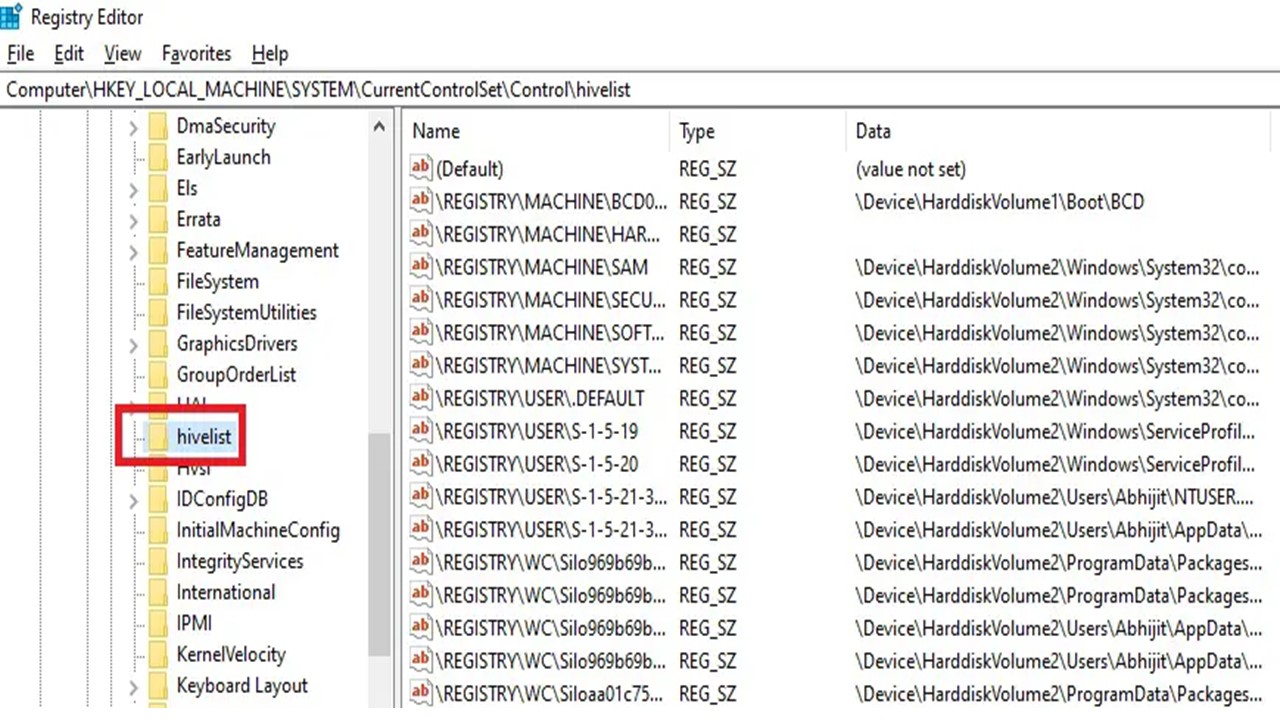
You can see the complete hive list of the Windows Registry on your computer. For that, simply run regedit to open it, and then steer to the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\hivelist key. The list will open as follows:
What are the Components of the Windows Registry?
In the Windows Registry you will find registry hives or folders that categorize the data stored in the registry. Then there are the registry keys or subfolders related to a specific type of data set.
And there are registry values containing the data affecting the programs, apps, operating system, and others.
However, ideally, the two main components of the registry are the keys and values. The keys may contain both subkeys and values.
The registry keys are pretty much the same as the folders and contain similar objects. Typically, there is a registry key for every Windows system and all the hives in the system are listed in it.
Every key in the registry acts as the starting point, often referred to as the root of the registry tree, while the subkeys and their values are located under the root.
The registry values, on the other hand, are much more similar to the files and are non-container objects.
These are actually settings by themselves. These refer to the name or data pairs and are referenced distinctly from the registry keys, though they are stowed within keys using a unique name written in non-case-sensitive letters.
If you take a deeper and closer look into the components of the Windows Registry, you will see that it is not just a simple, large file.
On the contrary, it is a set of files consisting of a large number of separate files. There are more folders within these hives.
These files are called hives, and each of them comprises a registry tree.
There are also a few supporting files in the different registry hives. These are as follows:
- HKEY_LOCAL_MACHINE\SAM: Sam, Sam.log, Sam.sav
- HKEY_LOCAL_MACHINE\SECURITY: Security, Security.log, Security.sav
- HKEY_LOCAL_MACHINE\SYSTEM: System, System.alt, System.log, System.sav
- HKEY_LOCAL_MACHINE\SOFTWARE: Software, Software.log, Software.sav
- HKEY_USERS.DEFAULT: Default, Default.log, Default.sav
- HKEY_CURRENT_CONFIG: System, System.alt, System.log, System.sav, Ntuser.dat, Ntuser.dat.log
There are some hives that do not have any associated files, are volatile, and are typically created and managed by the system in memory.
This means that these hives are temporary and are typically created every time the computer boots.
For example:
- HKEY_LOCAL_MACHINE\HARDWARE: Volatile hive
- HKEY_LOCAL_MACHINE\SYSTEM\Clone: Volatile hive
However, all these are database files, and can be read by only Kernel32, RegEdit, and Regedt32.
And, in Windows 2000, there is also a backup copy of the HKEY_LOCAL_MACHINE\System key stored. This helps in troubleshooting a problem.
What is the Purpose of a Registry?
The Windows Registry helps in operating and managing the computer. It mainly helps in configuring the settings of vital programs and applications and allows easy access to vital resources, data, information, and settings.
The different keys and values of the registry perform as the classified database of the system and allow for the storage of all vital information related to the different hardware and software installed in the computer.
This basically helps in finding out the errors in the system, if any, as well as monitoring the performance of the overall system.
It also helps advanced users, the tech support team, and administrators make changes both at the administrative and root levels to keep it operational.
In addition to that, the registry also helps in:
- Setting up and modifying access permissions
- Making changes in the software and hardware-level configurations
- Creating, renaming, removing, and manipulating, the keys, subkeys, values, and value data
- Exporting data in binary hive form
- Importing and exporting .reg files
- Bookmarking the keys selected by users as favorites
- Finding specific strings in value data, value, and key names
- Editing the registry of another computer within the network remotely
Most importantly, it creates a new key or folder while installing new software to store all relevant data and allow easy access.
Is It Safe to Edit the Registry?
No, unless you are sure and positive and know exactly what you are doing, it is not safe to edit the registry. This is because any errors may damage the system beyond repair.
Moreover, for your information, Microsoft typically does not support making any changes to the registry.
This is actually an action that should be performed by advanced and expert users, and that too after creating a proper backup of it so that errors can be undone and the system restored.
Therefore, exercise extreme caution while editing the registry, and never, ever, follow any edit suggestions from unofficial, unsolicited, or unreliable sources.
Or else, apart from causing serious damage to the operating system, erroneous registry editing may also have the following effect:
- It may cause instability in the system and even system collapse.
- It may corrupt the hard disk and the data stored on it.
- It will also cause problems while booting the system after you make changes to the stuff that you do not know well.
Therefore, to summarize, if you do not have the expertise, leave the registry alone to prevent breaking the operating system and having to reinstall it completely, which, needless to say, might result in a loss of data.
Where is the Registry Stored?
Ideally, in Windows 10, the registry and the system-wide settings are stored in files in the config folder, which is under C:\Windows\System32\Config\.
However, the user account of every Windows user has a separate NTUSER. dat file, which contains the user-specific keys and is under C:\Windows\Users\Name directory.
As for the set of discrete files in the registry, which are also referred to as registry hives as said earlier, these can be located in different folders, such as:
- HKEY_LOCAL_MACHINE\SAM: \system32\config\sam
- HKEY_LOCAL_MACHINE\SECURITY: \system32\config\security
- HKEY_LOCAL_MACHINE\SYSTEM: \system32\config\system
- HKEY_LOCAL_MACHINE\SOFTWARE: \system32\config\software
- HKEY_USERS.DEFAULT: \system32\config\default
- HKEY_USERS\UserProfile: \winnt\profiles\username
The system cache of the entire registry file, or a portion of it, is also stored in memory because it is the fundamental component of a Windows system and is accessed continuously during the operation.
Apart from that, the actual registry files, or hives, are also stored in:
- The %WINDIR% directory with Classes under the names System and User.dat
- %HOMEPATH%\NTUSER.DAT
As for the boot configuration, it is stored in [System Reserved]\Boot\BCD, which is also a registry hive.
Are Registry Keys Secure?
Yes, the registry keys are quite secure by themselves since they are protected by Access Control Lists or ACLs. In spite of that, these keys are not secure enough to store passwords and other secrets in plain text.
Ideally, since the registry itself is centralized, security may be compromised while working with the registry and may allow unwanted access to protected information and system resources.
Moreover, you can add to the security aspect even more by:
- Making changes in the operating system
- Modifying permissions to access files and directories
- Registry key edits and auditing
- Adding to the physical security of the system registry
- Restricting remote access to the registry
- Using a Security Configuration Manager (SCM)
- Editing the configuration file
- Configuring the system and performing analysis from the command line or otherwise
- Transferring the configuration to a database
- Maintaining consistency in configurations
All in all, it can be safely said that the registry key will not cause any harm in and of itself because one must have the necessary permissions to access the registry in the first place.
Advantages
- It involves only a small number of files for restore actions and backups of the configuration.
- It replaces text-based configuration files with strongly typed data.
- The files are typically stored in known locations.
- It allows users to use Group Policy to set policies and manage programs centrally.
- Files can be collaborated on most efficiently.
- It offers security and keeps things tidy.
- It permits remote support and management since it can be accessed by using a network connection.
- User and machine configuration are loaded from a user-specific path and a read-only system location, respectively, making each separate.
- Configuration data storage across a variety of apps is more standardized.
- Parsing is not required to access the registry, which makes it quick to read and write as compared to the Initialization or INI file.
- Support personnel and administrators have to pre-set or pre-configure only a few options since parts of the settings are saved in a text-based .reg file that can be edited easily using a text editor.
- The database-like features of the registry offer atomic updates.
- It maintains overall constancy when the same registry value is updated at the same time, as a change in one process will precede that in the other.
Disadvantages
- It depends mainly on the local machine.
- It is tedious to transfer the user settings of each program between different systems.
- A lot of erroneous and junk data is left behind or added when apps are uninstalled.
- It may cause issues such as incorrect icons and file associations due to a large amount of unrepaired damage and useless data accumulation.
- The file or set of files is pretty small and can be located anywhere, which makes the access costs pretty high.
- Due to the small number of files, the failure points are quite large in number.
- Being centralized, a corrupt registry can put the entire system into trouble and make recovering and backing up each app pretty difficult.
- Its binary and opaque nature makes repairing very difficult in an event of damage caused by errors.
- Due to complicated navigation and being monolithic, the settings of the apps are less portable if put in the registry.
- It has to be in sync with the file system and repeat a lot of its functionality, which is a complete violation of the Don’t Repeat Yourself (DRY) Principle.
- Booting of the system can be prevented by a damaged registry because the information needed to load the device drivers is stored in it.
- App settings and configuration cannot be moved by copying and pasting of files simply. It needs the full restoration of software from original media.
- It is necessary to process the whole file once for every boot since the registry is centralized in nature.
Conclusion
This article clearly explains the utility of the Windows Registry, though it may be a bit difficult to navigate and use for some users.
However, with the varied components and advantages offered by the registry, Windows users typically have the assurance of overall system security and consistency in the process.